[EN] Password authentication bypass in authentik - CVE-2024-47070
During one of our penetration tests last year, we discovered an interesting critical vulnerability - an authentication bypass in authentik, an open-source identity provider.

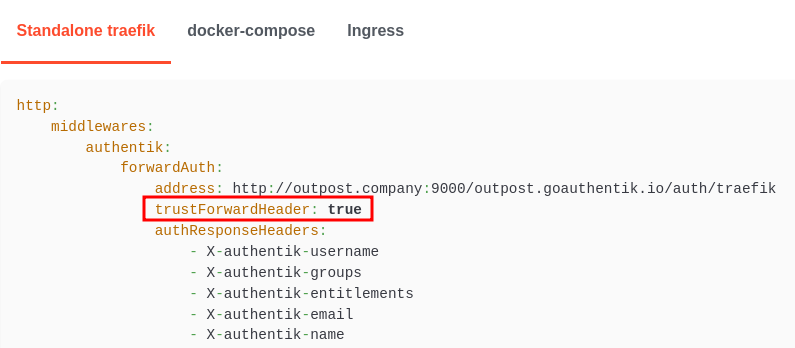
As part of our tests, we checked whether it was possible to spoof a user’s IP address by adding the X-Forwarded-For header to an HTTP request. This is a common test performed during a pentest to assess reverse proxy configurations. Interestingly, authentik’s documentation for Traefik setup includes the setting trustForwardHeader: true, meaning many instances following this guide may have this configuration applied.
After confirming that the IP address could be spoofed, we also tested for a Cross-Site Scripting (XSS) vulnerability in the Sessions List view, where the user’s IP address is reflected. To do this, we added X-Forwarded-For: <img src=0 onerror=alert(1)> header to the request and attempted to log in. However, by accident, the tester mistyped the password… and the login still succeeded.
Upon further examination, the authentication bypass became clear. The vulnerability allowed users to bypass password authentication by adding an X-Forwarded-For header with an unparsable IP address, e.g., “a”. This made it possible to log in to any account with a known username or email address.
Steps to reproduce:
- Navigate to
/if/flow/default-authentication-flow. - Enter
akadminas the username and press Enter. - Type anything in the password field, intercept the HTTP request, and add the header
X-Forwarded-For: a. - Refresh the page - you should now be logged in as the
akadminuser.
Proof of Concept Video:
We promptly reported the vulnerability to the authentik team and had a smooth disclosure process. The issue was patched in authentik versions 2024.6.5 and 2024.8.3.
The vulnerability received a CVSS score of 9.0/10, classifying it as Critical severity (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:C/C:H/I:H/A:H).

This case is a great example of how penetration testing can sometimes uncover critical issues in unexpected places, reinforcing the value of thorough and exploratory testing.
More information:
Authentik Security Advisory – CVE-2024-47070
GitHub Security Advisory – GHSA-7jxf-mmg9-9hg7